Strengthening Cyber Defenses with Expert-Led Security Testing
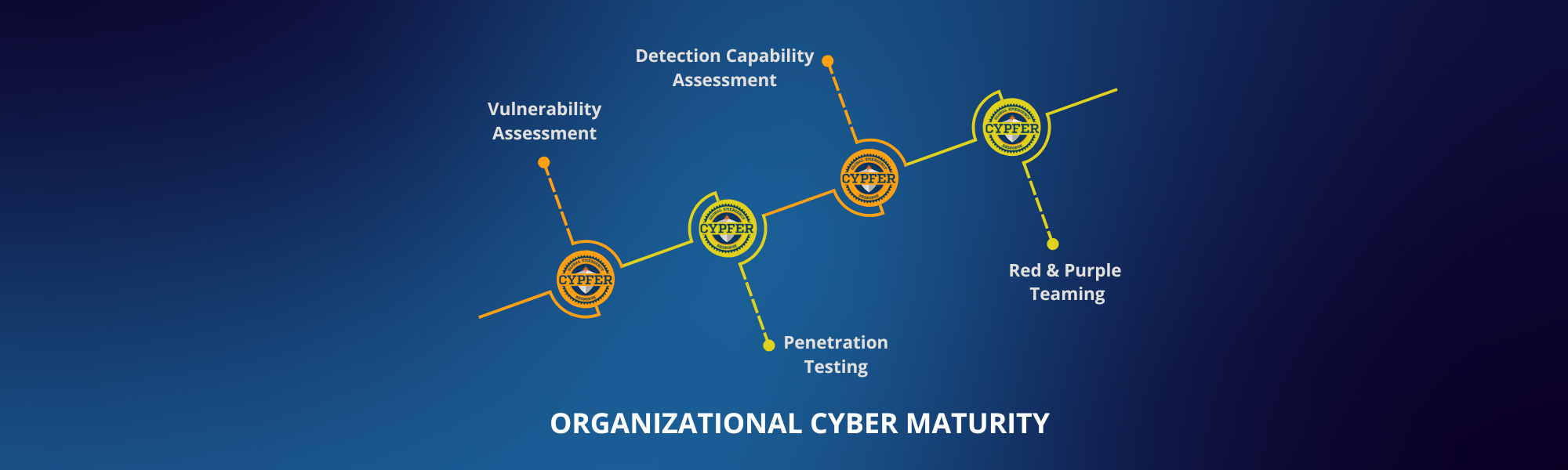
Cyber threats are evolving at an alarming pace, leaving organizations struggling to keep up. Security testing isn’t just a checkbox for compliance—it’s an essential pillar of cyber resilience. But how do you ensure that your defenses are truly prepared? The journey toward cyber maturity requires a structured approach, moving from basic vulnerability assessments to advanced red teaming exercises.
This special article, written by Martin Verreault from CYPFER’s Offensive Security team, provides an expert perspective on the different types of security testing, their unique value, and how often they should be performed. Whether you’re looking to uncover vulnerabilities, test your detection capabilities, or simulate real-world attacks, this guide will help you navigate the critical steps needed to achieve the highest level of cyber maturity.
Vulnerability Assessment
This is an exercise where you identify vulnerabilities on your systems through automated scanning tools. If configured correctly, these tools will provide visibility on missing security patches as well as misconfigurations. Typically, these tools will focus on the IT infrastructure vulnerabilities and will most likely not identify intricate vulnerabilities in web applications. Moreover, the severity score they will assign to each vulnerability will be based on the software manufacturer Common Vulnerability Scoring System (CVSS) score and won’t necessarily represent the actual level of cyber risk for your organization. Nevertheless, performing frequent vulnerability assessments, prioritizing and remediating vulnerabilities according to their actual level of risk are the cornerstone of an organization vulnerability management program.
Penetration Testing
A penetration test (pentest) is a thorough security assessment designed to evaluate the vulnerabilities on your systems. The following types of penetration tests are among the most popular:
- External network: testing the security of your internet facing systems. This test will typically focus on the IT infrastructure and easily identifiable vulnerabilities in exposed web applications.
- Internal network: testing the security of your internal systems. This test will typically focus on servers as well as Active Directory / Entra ID (Azure) services exposed to internal users.
- Web application: testing the security of a web application from the point of view of an anonymous or an authenticated attacker using the various roles within the application.
This exercise includes both automated scans and manual testing to identify misconfigurations and weaknesses. Vulnerabilities may be actively exploited during the test to demonstrate their potential impact. As a result, you should receive a comprehensive report that highlights risks based on the impact and likelihood of the exploitation for each identified vulnerability. A pentest is not a vulnerability assessment, meaning the report only includes information about vulnerabilities that were exploited. During the scoping or kickoff call, you may establish goals with the penetration tester, such as compromising the domain or accessing critical assets.
Generally, we recommend that organizations at least perform one external and one internal penetration test per year or after important changes to their IT infrastructure or cloud services. Organization relying on custom web applications for their core business should also perform regular in-depth penetration testing of these applications. Organizations that recently suffered from a data breach or acquired a new company should also perform penetration testing to uncover vulnerabilities that could be exploited and cause serious impacts to the organization. Finally, industry standards and regulations, such as the Payment Card Industry Data Security Standard (PCI DSS), require organizations to regularly perform penetration tests according to specific criteria.
Detection Capability Assessment
A Detection Capability Assessment (DCA) is designed to evaluate your detection and response capability by executing Tactics, Techniques & Procedures (TTPs) used by threat actors such as ransomware gangs. Typically, about 20 to 25 of these TTPs are executed within your network during live sessions where your detection team (blue team) attempts to identify the activities. In contrast to a red team exercise, this exercise is performed in a fully transparent and collaborative manner with the blue team. As a result of a DCA, you will be able to identify detection and response strengths and gaps in the following areas: cloud, network, malicious execution, lateral movement, and vulnerability exploitation. The report you will receive documents each test case and the outcome based on evidence shared by your blue team during the exercise. Each test case is tied to the TTPs and categorized according to the MITRE ATT&CK framework, an industry standard.
DCAs are typically designed to assess mature environments with detection capabilities in place. If you have recently changed your security stack (e.g., new Endpoint Detection and Response solution – EDR), you could benefit from a DCA to evaluate your new detection capabilities. You can also improve your blue team capabilities with this assessment since it acts as a training opportunity to understand the adversary mindset. Ideally, you should perform DCA at least once a year to retest TTPs that you did not detect in a previous assessment and to test for the latest TTPs.
Red and Purple Teaming
A red team exercise typically combines the following phases: external reconnaissance and testing, phishing and physical intrusion, and internal network testing. The red team focuses on compromising assets that are valuable to you while assessing your blue team detection and response capabilities. During the exercise, red teamers will attempt to compromise the environment using stealth techniques to avoid early detection by the blue team, like a sophisticated threat actor would do. This type of testing should not be announced in advance to the blue team to emulate real-world conditions. As the exercise progresses, the level of stealth may be reduced to identify the detection threshold. A red team exercise answers the question: can I detect a threat actor in my environment before it is too late?
The purple team exercise follows the completion of the red team exercise and focuses on identifying gaps in your detection capabilities based on the activities performed during the exercise. It is designed as a collaboration with the blue team during live sessions to improve the team detection capabilities based on the attacks performed. Similarly to the DCA but with the added element of surprise related to an unannounced attack, the blue team will benefit from this activity as a form of live training in their environment.
Red and purple team exercises are typically designed to assess mature environments with detection capabilities in place that were already tested as part of a DCA or a similar exercise. Small red team exercises typically last at least 4 weeks, while regular red team exercises last between 8 to 10 weeks. Ideally, for mature organizations with a dedicated blue team improving detection controls on a continuous basis, you should perform a red team at least once a year.
CYPFER’s Dedicated Team – Your Offensive Security Experts
At CYPFER, security testing isn’t just a service—it’s a mission. Our dedicated offensive security team consists of elite experts in vulnerability assessment, penetration testing, detection capability assessment, and red teaming. We operate at the highest level of precision, leveraging real-world adversary tactics to expose weaknesses before they become liabilities.
- Penetration Testing: Identifying and exploiting vulnerabilities to strengthen your cyber posture.
- External network: internet-facing systems.
- Internal network: internal servers, Active Directory and Entra ID (Azure).
- Web application: all roles and functions within a web application.
- Detection Capability Assessment (DCA): Collaborating with your blue team to assess and improve your detection and response capabilities.
- Red & Purple Teaming: Simulating real-world attacks and assessing if your blue team can detect a sophisticated threat actor living in your environment.
With CYPFER’s offensive security specialists, you don’t just test your defenses—you fortify them. Our global, 24/7 team works shoulder-to-shoulder with organizations to enhance security maturity, ensuring you’re always one step ahead of cyber threats.
Cyber Certainty™ starts here. Let CYPFER’s offensive security experts help you build an impenetrable security posture today.
Your Complete Cyber Security Partner:
Every Step, Every Threat.
At CYPFER, we don’t just protect your business—we become part of it.
As an extension of your team, our sole focus is on cyber security, ensuring your peace of mind. From incident response and ransomware recovery to digital forensics and cyber risk, we integrate seamlessly with your operations. We’re with you 24×7, ready to tackle threats head-on and prevent future ones.
Choose CYPFER, and experience unmatched dedication and expertise. Trust us to keep your business secure and resilient at every turn.

Get Cyber Certainty™ Today
We’re here to keep the heartbeat of your business running, safe from the threat of cyber attacks. Wherever and whatever your circumstances.
Contact CYPFER





